What Is Cybersecurity Risk Management?
Cybersecurity risk management is a strategic approach to prioritizing threats. Organizations implement cybersecurity risk management in order to ensure the most critical threats are handled in a timely manner. This approach helps identify, analyze, evaluate, and address threats based on the potential impact each threat poses.
A risk management strategy acknowledges that organizations cannot entirely eliminate all system vulnerabilities or block all cyber attacks. Establishing a cybersecurity risk management initiative helps organizations attend first to the most critical flaws, threat trends, and attacks.
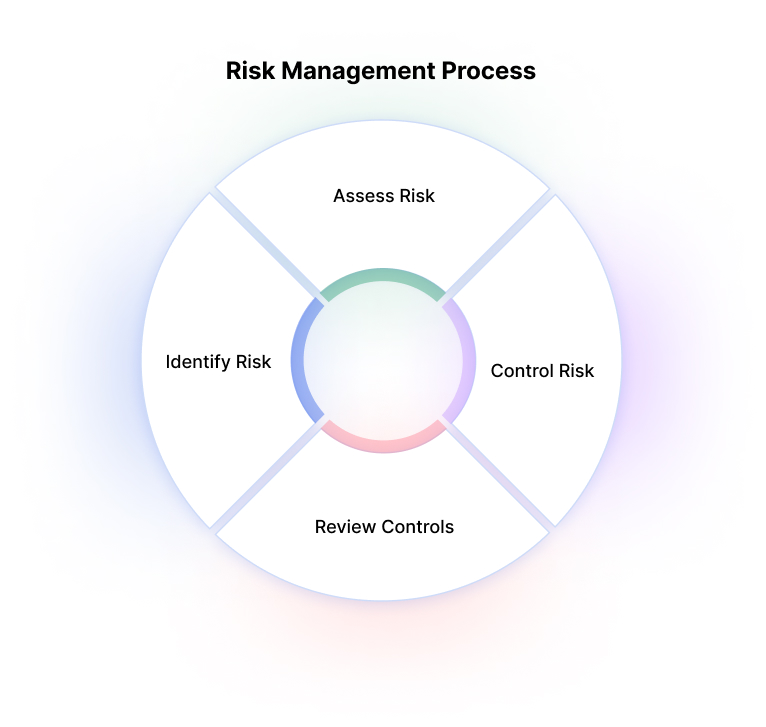
Broadly speaking, the cybersecurity risk management process involves four stages:
- Identifying risk – evaluating the organization’s environment to identify current or potential risks that could affect business operations
- Assess risk – analyzing identified risks to see how likely they are to impact the organization, and what the impact could be
- Control risk – define methods, procedures, technologies, or other measures that can help the organization mitigate the risks.
- Review controls – evaluating, on an ongoing basis, how effective controls are at mitigating risks, and adding or adjusting controls as needed.
What is a Cybersecurity Risk Assessment?
A cybersecurity risk assessment is a process that helps organizations determine key business objectives and then identify the appropriate IT assets required to realize their objectives.
It involves the identification of cyber attacks that may negatively impact these IT assets. The organization is required to determine the likelihood of the occurrence of these attacks, and define the impact each attack may incur.
A cybersecurity risk assessment should map out the entire threat environment and how it can impact the organization’s business objectives.
The result of the assessment should assist security teams and relevant stakeholders in making informed decisions about the implementation of security measures that mitigate these risks.
What Are Cyber Threats?
The term cyber threat generally applies to any vector that can be exploited in order to breach security, cause damage to the organization, or exfiltrate data.
Common threat categories facing modern organizations include:
- Adversarial threats—including third-party vendors, insider threats, trusted insiders, established hacker collectives, privileged insiders, ad hoc groups, suppliers, corporate espionage, and nation-states. This category also includes malicious software (malware) created by any of these entities. Large organizations mitigate these threats by establishing a security operations center (SOC) with trained security staff and specialized tooling.
- Natural disasters—hurricanes, floods, earthquakes, fire, and lightning can cause as much damage as a malicious cyber attacker. A natural disaster can result in loss of data, disruption of services, and the destruction of an organization’s physical or digital resources. The threat of natural disaster can be minimized by distributing an organization’s operations over multiple physical sites or using distributed cloud resources.
- System failure—when a system fails, it may cause data loss and also lead to a disruption in business continuity. Make sure that your most critical systems are running on high-quality equipment, have redundancy in place to ensure high availability, are backed up, and your providers offer timely support.
- Human error—any user may accidentally download malware or get tricked by social engineering schemes like phishing campaigns. A storage misconfiguration may expose sensitive data. To prevent and mitigate these threats, you should establish an employee training program and enforce strong security controls. For example, use password managers and monitor critical systems for misconfigurations.
Here are key threat vectors that affect the majority of organizations:
- Unauthorized access—may be the result of malicious attackers, malware, and employee error.
- Misuse of information by authorized users—an insider threat may misuse information by altering, deleting, or using data without authorization.
- Data leaks—threat actors or cloud misconfiguration may lead to leaks of personally identifiable information (PII) and other types of sensitive data.
- Loss of data—poorly configured replication and backup processes may lead to data loss or accidental deletion.
- Service disruption—downtime may cause reputational damages and revenue losses. It may be accidental, or the result of a denial of service (DoS) attack.
Cyber Risk Management Frameworks
There are several cyber risk management frameworks, each of which provides standards organizations can use to identify and mitigate risks. Senior management and security leaders use these frameworks to assess and improve the security posture of the organization.
A cyber risk management framework can help organizations effectively assess, mitigate, and monitor risks; and define security processes and procedures to address them. Here are several commonly used cyber risk management frameworks.
NIST CSF
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a popular framework. The NIST CSF framework provides a comprehensive set of best practices that standardize risk management. It defines a map of activities and outcomes related to the core functions of cybersecurity risk management—protect, detect, identify, respond, and recover.
ISO 27001
The International Organization for Standardization (ISO) has created the ISO/IEC 270001 in partnership with the International Electrotechnical Commission (IEC). The ISO/IEC 270001 cybersecurity framework offers a certifiable set of standards defined to systematically manage risks posed by information systems. Organizations can also use the ISO 31000 standard, which provides guidelines for enterprise risk management.
DoD RMF
The Department of Defense (DoD) Risk Management Framework (RMF) defines guidelines that DoD agencies use when assessing and managing cybersecurity risks. RMF splits the cyber risk management strategy into six key steps—categorize, select, implement, assess, authorize, and monitor.
FAIR Framework
The Factor Analysis of Information Risk (FAIR) framework is defined for the purpose of helping enterprises measure, analyze, and understand information risks. The goal is to guide enterprises through the process of making well-informed decisions when creating cybersecurity best practices.
Best Practices for Cybersecurity Risk Assessment
Build Cybersecurity into the Enterprise Risk Management Framework
Fully incorporate your risk-based cybersecurity program into the enterprise risk management framework, which functions as the organizing principle for analyzing and classifying enterprise risks. The framework should not be used as a general guideline, but rather as the organizing principle. By framing cyber risk as a business risk, this approach makes cyber risk management more intelligible to businesses.
Identify Value-Creating Workflows
Identify the workflows that generate the greatest business value and define their associated risks. It is important to consider the potential impact of crucial workflows because these can also pose a significant risk. For example, payment processes create value but present a business risk, as they are vulnerable to fraud and data leakage.
Make sure the cybersecurity team knows which processes are regarded as valuable for your organization, and define the components (data assets, tools, teams) involved in each process. This allows you to apply the recommended controls. A collaborative approach involving both cybersecurity and business personnel is more effective than the one-sided maturity-based approach.
Prioritize Cyber Risks
Determine risk level based on the cost of prevention and value of information to inform your risk management and mitigation procedures. High-level risks should be addressed as soon as possible, while low-level risks can be addressed down the line or accepted as a tolerated risks. If the cost of protecting an asset is higher than its value, the expense is not worthwhile unless the risk may impact your reputation.
Implement Ongoing Risk Assessments
Perform continuous, adaptive, and actionable risk identification and assessment to keep up with evolving cybersecurity threats and solutions. Regularly review risk management processes to identify and remediate gaps. Cybersecurity teams rely on actionable insights from risk assessments to secure digital environments and assets.
Cybersecurity Risk Management with Imperva
Imperva can help organizations identify and manage cybersecurity risks across two broad categories – application security and data security.
Imperva Application Security
Imperva provides comprehensive protection for applications, APIs, and microservices:
Web Application Firewall – Prevent attacks with world-class analysis of web traffic to your applications.
Runtime Application Self-Protection (RASP) – Real-time attack detection and prevention from your application runtime environment goes wherever your applications go. Stop external attacks and injections and reduce your vulnerability backlog.
API Security – Automated API protection ensures your API endpoints are protected as they are published, shielding your applications from exploitation.
Advanced Bot Protection – Prevent business logic attacks from all access points – websites, mobile apps and APIs. Gain seamless visibility and control over bot traffic to stop online fraud through account takeover or competitive price scraping.
DDoS Protection – Block attack traffic at the edge to ensure business continuity with guaranteed uptime and no performance impact. Secure your on premises or cloud-based assets – whether you’re hosted in AWS, Microsoft Azure, or Google Public Cloud.
Attack Analytics – Ensures complete visibility with machine learning and domain expertise across the application security stack to reveal patterns in the noise and detect application attacks, enabling you to isolate and prevent attack campaigns.
Client-Side Protection – Gain visibility and control over third-party JavaScript code to reduce the risk of supply chain fraud, prevent data breaches, and client-side attacks.
Imperva Data Security
Imperva protects all cloud-based data stores to ensure compliance and preserve the agility and cost benefits you get from your cloud investments
Cloud Data Security – Simplify securing your cloud databases to catch up and keep up with DevOps. Imperva’s solution enables cloud-managed services users to rapidly gain visibility and control of cloud data.
Database Security – Imperva delivers analytics, protection and response across your data assets, on-premise and in the cloud – giving you the risk visibility to prevent data breaches and avoid compliance incidents. Integrate with any database to gain instant visibility, implement universal policies, and speed time to value.
Data Risk Analysis – Automate the detection of non-compliant, risky, or malicious data access behavior across all of your databases enterprise-wide to accelerate remediation.